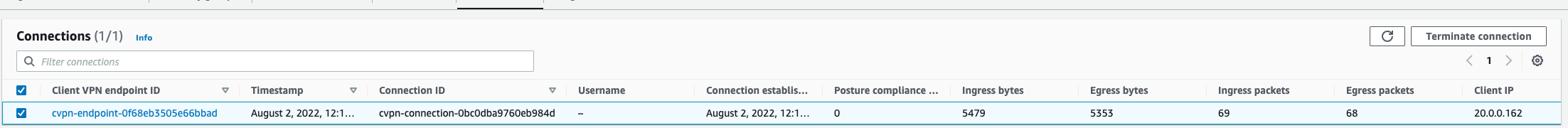
Latest AWS Managed Client VPN Connection
Abstract
Creating and managing VPN connections to AWS Cloud Networks is a regular task that we periodically face with. One of the communication channels is VPN connection. For a while if you want to establish VPN connection you have to spin up EC2 instance from AMI in the Marketplace that has preinstalled and configured OpenVPN, or DIY - setup OpenVPN from the scratch and configure it. It takes time and resources to manage such setups. But AWS has released managed vpn-client service. Let’s go through bootstrap process and check its compatibilities.
Target Architecture Diagram
Here is a Client VPN ecosystem and its integration point when auto provisioning as a managed service in AWS Cloud:
- client VPN Endpoint (main entry point with 443 port)
- AWS ACM with Client/Server certificates that are establishing secure connection
- Target SN association to interact with resources
- Internet GW, DNS server
- Connection handler Lambda that can be easily integrated by ARN with connection requests
Let’s go through setup process and look to each component.
Everything start with Certificate generation:
1
2
3
4
5
6
git clone https://github.com/OpenVPN/easy-rsa.git
cd easy-rsa/easyrsa3
./easyrsa init-pki
./easyrsa build-ca nopass
./easyrsa build-server-full server nopass
./easyrsa build-client-full client1.domain.tld nopass
Copy server certificate and key and client cert and key to custom folder:
1
2
3
4
5
6
7
mkdir ~/custom_folder/
cp pki/ca.crt ~/custom_folder/
cp pki/issued/server.crt ~/custom_folder/
cp pki/private/server.key ~/custom_folder/
cp pki/issued/client1.domain.tld.crt ~/custom_folder
cp pki/private/client1.domain.tld.key ~/custom_folder/
cd ~/custom_folder/
Upload server cert and key and client cert and key to ACM
1
2
3
aws acm import-certificate --certificate fileb://server.crt --private-key fileb://server.key --certificate-chain fileb://ca.crt --region us-east-1 <aws:playgroud-ops:DevUser>
{
"CertificateArn": "arn:aws:acm:us-east-1:123456789012:certificate/a828"
1
2
3
aws acm import-certificate --certificate fileb://client1.domain.tld.crt --private-key fileb://client1.domain.tld.key --certificate-chain fileb://ca.crt --region us-east-1 <aws:playgroud-ops:DevUser>
{
"CertificateArn": "arn:aws:acm:us-east-1:123456789012:certificate/8ce1"
After uploading this certificates will be available at AWS ACM and are ready to be associated in authentication.
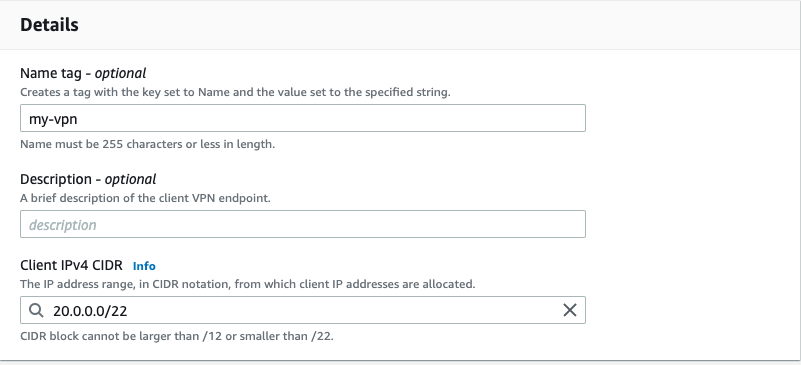
Create VPN Client
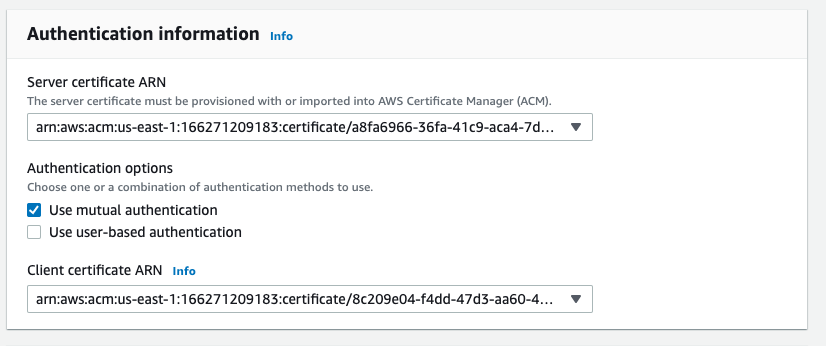
VPN connection authentication:
Now it’s time to attach uploaded certificates by ARN to client vpn.
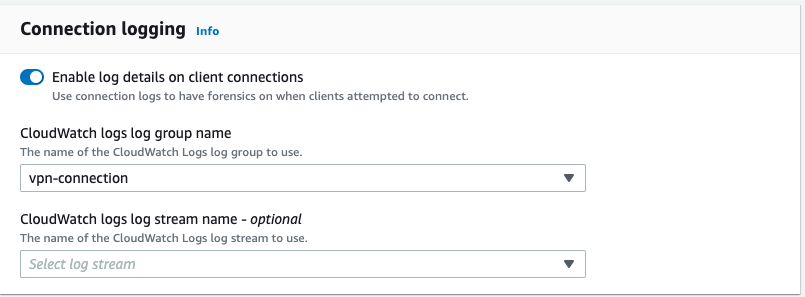
Connection logging
Additionally, Client VPN support CloudWatch logging for multiple metrics.
Connection handling
We can enable connection handling and specify the lambda function that will be trigger on connection events. 
Enable split tunnel
Choose transport TCP or UDP. Split tunnel parameter controls either all traffic will be routed to AWS Cloud or only traffic related to AWS IP range. 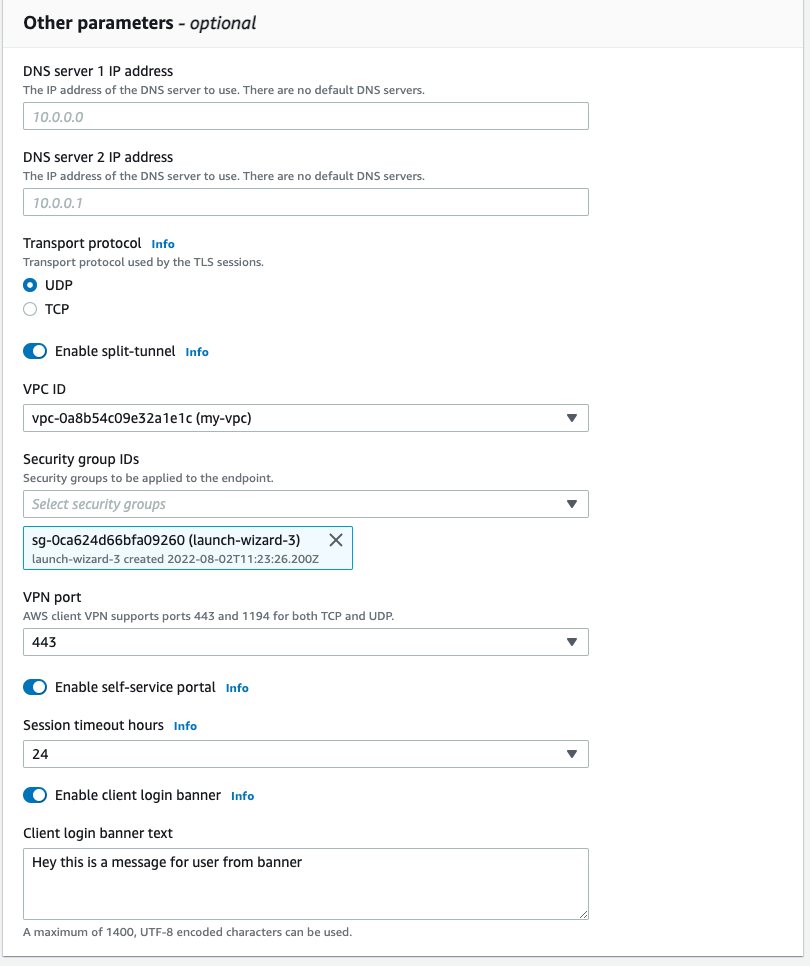
Create VPN client:
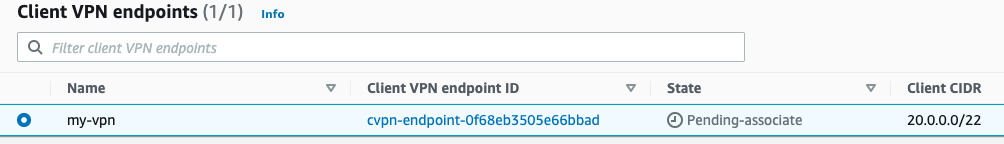 On completing the wizard, vpn client status is in Pending-associate mode - we need associate SN with this endpoint
On completing the wizard, vpn client status is in Pending-associate mode - we need associate SN with this endpoint
Create association:
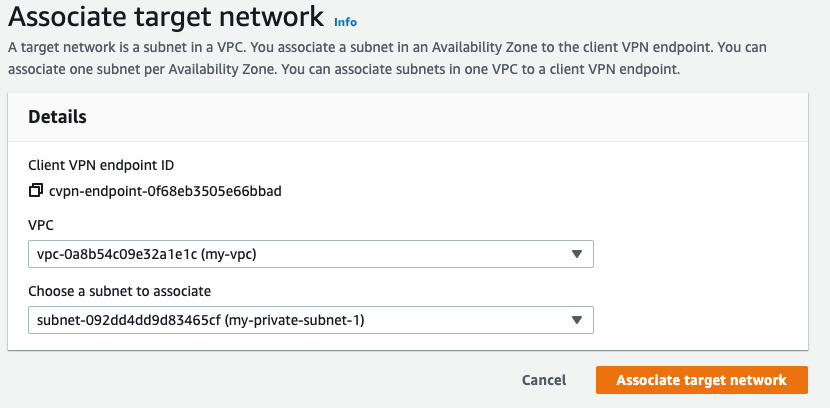 Once Target Subnet is associated, it will take 5-10 min to complete the setup.
Once Target Subnet is associated, it will take 5-10 min to complete the setup.
Create authorization rules:
Authorization rules allow to narrow the NW addresses for connection to endpoint 
Download OVPN configuration file from AWS Console
Now it’s time to download ovpn file that can be directly imported into OpenVPN Client.
This configuration file does not have all required information, so we should manualy update host name, add sections with client certificates according to following instructions: https://docs.aws.amazon.com/vpn/latest/clientvpn-admin/cvpn-getting-started.html
After importing configuration into OpenVPN Connect vpn channel is setup:
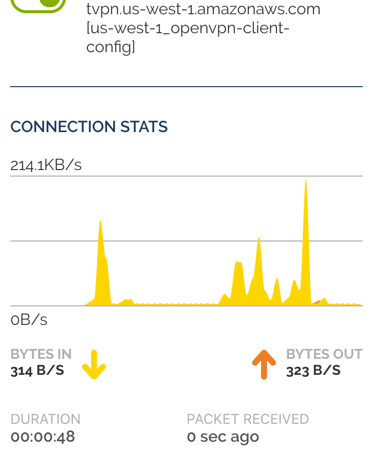
Check CloudWatch metrics:
CloudWatch provides excellent views to monitor the data transfer per each connection, log individual sessions and connection pull. 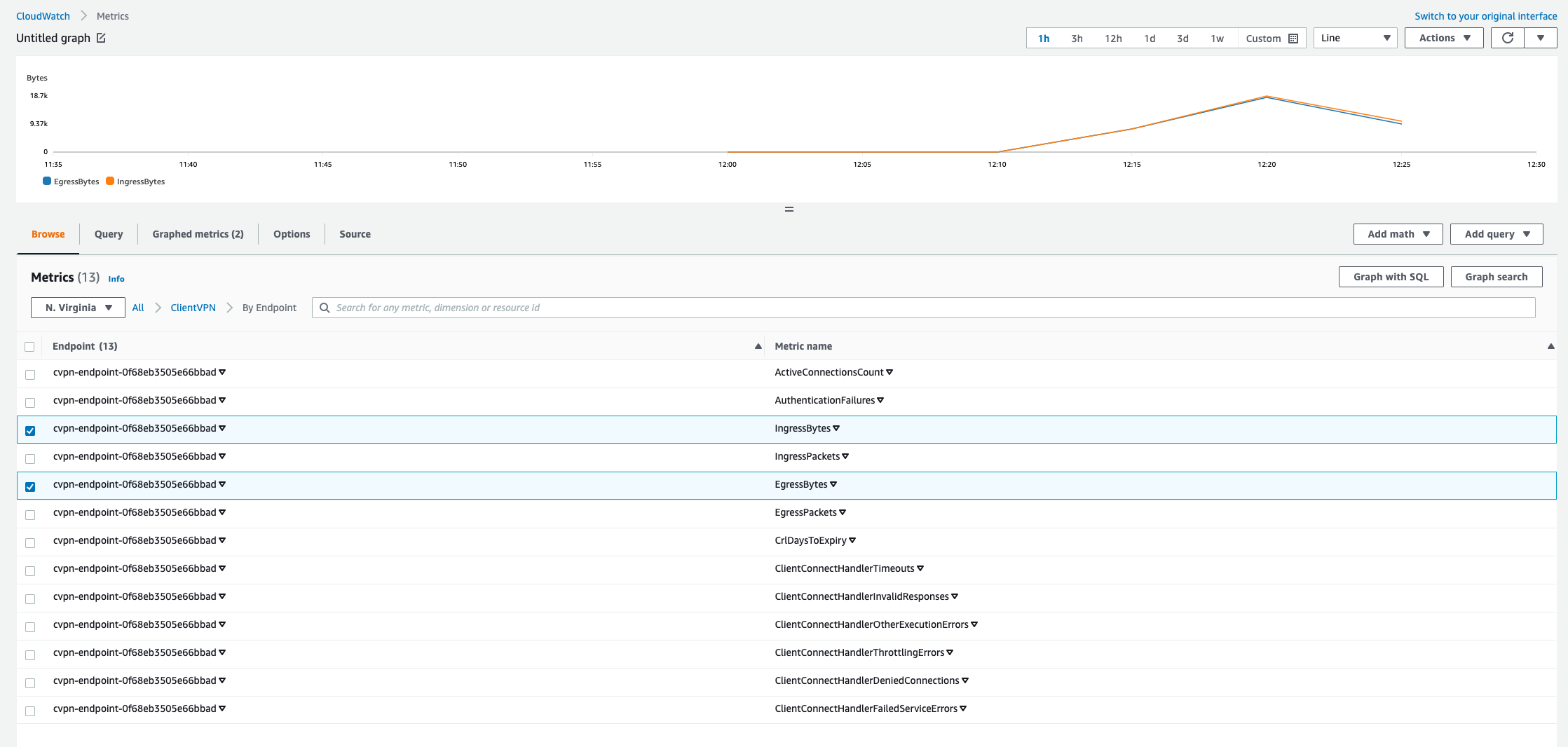
Double-Check Client-VPN status from CLI:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
aws ec2 describe-client-vpn-endpoints --region=us-west-1
{
"ClientVpnEndpoints": [
{
"ClientVpnEndpointId": "cvpn-endpoint-123456789012",
"Description": "Client VPN example",
"Status": {
"Code": "available"
},
"CreationTime": "2023-09-10T11:39:05",
"DnsName": "*.cvpn-endpoint-123456789012.prod.clientvpn.us-west-1.amazonaws.com",
"ClientCidrBlock": "10.20.0.0/22",
"DnsServers": [
"8.8.8.8"
],
"SplitTunnel": false,
"VpnProtocol": "openvpn",
"TransportProtocol": "udp",
"VpnPort": 443,
"ServerCertificateArn": "arn:aws:acm:us-west-1:123456789012:certificate/7d00",
"AuthenticationOptions": [
{
"Type": "certificate-authentication",
"MutualAuthentication": {
"ClientRootCertificateChain": "arn:aws:acm:us-west-1:123456789012:certificate/cd2e"
}
}
],
"ConnectionLogOptions": {
"Enabled": false
},
"Tags": [
{
"Key": "environment",
"Value": "ovpn"
}
],
"SecurityGroupIds": [
"sg-0bb8"
],
"VpcId": "vpc-1",
"ClientConnectOptions": {
"Enabled": false,
"Status": {
"Code": "applied"
}
},
"SessionTimeoutHours": 24,
"ClientLoginBannerOptions": {
"Enabled": false
}
}
]
}
Conclusions:
AWS Client VPN makes process of vpn connection setup much more secure and easier compared to DIY EC2-based vpn server. In the next post Automating AWS Client VPN creation with Terraform and Scripts we will automate its setup using Terraform and scripts to make setup process even faster and robust.